Gateway
Category:
VM
This CTF provided a VM which encompassed a number of different challenges, the first part of which is
to actually access it. When booting up the VM, we find that the drive it's accessing is
encrypted and you need a passkey to decrypt it. Luckily there is an unencrypted drive that is
accessible.
To access this, we need to add a live CD to the VM so that we can boot off that instead.
I chose to use Kali Linux for this. Once we boot into Kali, we can access the unencrypted
drive which is labeled "Boot".
Right away there is a file that stands out: "usefultool.exe"
Running this we discover that it is just a program that ROT13's whatever string you provide, so
this is a pretty good indicator that our flag will be a ROT13 that needs to be decoded.
Looking around the drive more, nothing of use was really found, so I took a closer look at the
.exe. Running strings on it I found something interesting.
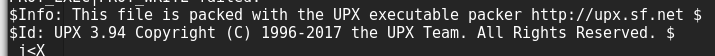
However, this turned out to only be part of the flag. Looking closer at the strings output,
it seems that the exe has been packed with UPX. Using UPX to unpack it, we can finally get the full
output of all the strings, as well as our full ROT13 flag.

Decoding it we get our flag as well as the password to unencrypt the drive.

Challenge:
Leap of Faith
Category:
VM

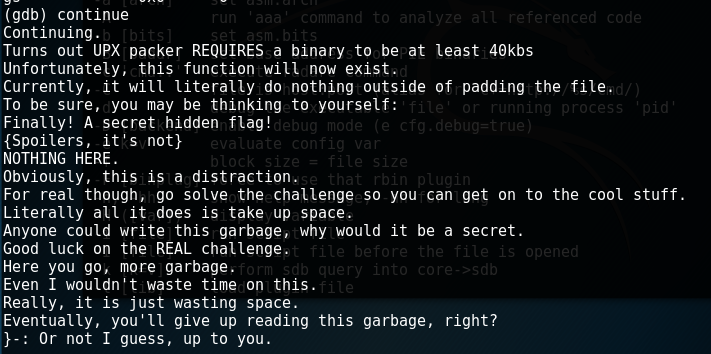
This challenge utilized the same exe from the previous challenge. I overthought this one a lot, but looking at all the strings in GDB by accessing the function 'randomPaddingFunction' that I was told to ignore, I finally realized that the first letter of each string gave the flag!
Challenge:
Worth a Thousand Words
Category:
VM

In the photos folder on the VM there are three different jpgs. Each one contains a part of the flag.
Using strings on 1.jpg we get the first part which is just TUCTF{.

2.jpg has a hidden file inside of it and we can extract it with binwalk. Dumping the contents we get our second part of the flag: Devils

3.jpg is corrupted and needs to be fixed before we can open it. This took a bit of research, but once I found which portions of the IHDR were wrong, I was able to edit it in hexeditor and make it so we can see the image. Running pngcheck helped confirm when it was actually uncorrupted.
Broke:

Edited:

Opening the image, there is a barcode on the screen in the picture, and scanning this gives us the final part of the flag: InThePixels}


Challenge:
Euchlid Go Away
Category:
VM
This was one of my favorite challenges of the CTF. Remoting in with netcat, we are dropped into a text-based game. There is a lot of messaging about a rumored hidden room, so I guessed this is exactly what needed to be found.

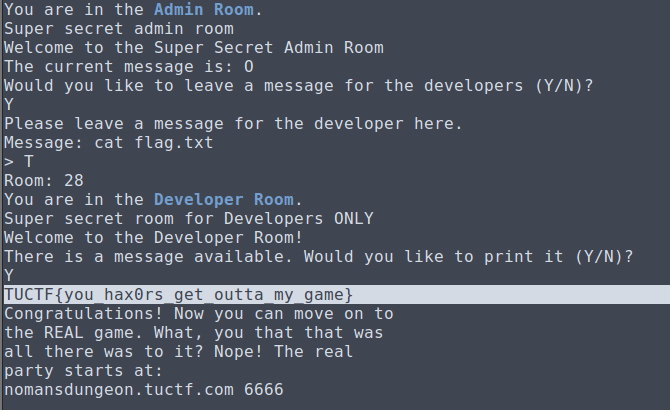
There were a couple tricks to this: first, we need to be admin, which I guessed would give us some extra powers. Messaging an admin in the game reveals their username, so I took that and logged back in under that admin name.
Next, I sent a message that I had bugged leveling and increased my level past the normal user cap of 255 and make myself 256.
Upon doing so we are identified as admin and we have some newfound powers!

One of which is the ability to teleport and a map of all the rooms.
Teleporting to the admin room first, there was a function to leave messages for the devs. I immediately thought to input "cat flag.txt". After this, I teleported to the dev room and it gave me the option to read the message I left for myself. This executed the action I left in the message, and I got the flag!
0 comments:
Post a Comment
Note: Only a member of this blog may post a comment.