Zico2
Objective:
Get root
Loading up the VM in VirtualBox, it's time to do another round of arp-scan and Nmap to find out our target IP address and enumerate on what ports/services are open to us.

Jumping right in to port 80, we load up the website in a browser. There's a bunch of stuff on this site.

Quite a bit to look at, but clicking on the tools section, the URL tickled the part of me that wants to test out directory traversal. Sure enough, it works, and we can see the /etc/passwd file. I looked around a bit more but nothing else really stood out.

Next, I booted up Dirb using a common wordlist, and tried to see if there were any directories hidden from us.

The /dbadmin directory looks like it could be tasty.
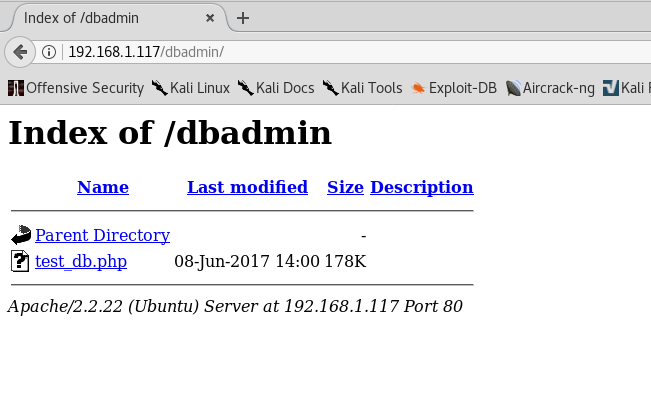

Nice--a login screen. Does 'admin' work for the password?

Lol... yep. Bad, bad, bad, Mr. Admin, sir. You should always change the default password! So we have a phpLiteAdmin v1.9.3 running on this system. Searching on Exploitdb, I found just what we needed, which fit this version perfectly:

I tested this out by following the PoC steps, and it worked like a charm.

Now we can get creative and think of a way to get a reverse shell going. I initially tried using the PHP reverse shell code from Pentest Monkey, but it was having a bit of trouble going through, and while I try to avoid Msfvenom/metasploit when possible, I decided to just go for it this time. I generated a reverse shell and then hosted it on my box using Python's simpleHTTPserver.

After my server was running, I created a new table in the database with the following php code as the default text:

Then I setup a listening port and got ready to deploy this shell.
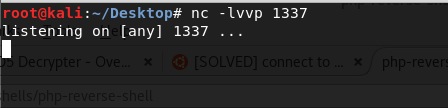

Executing it via our directory traversal bug we found earlier, the system downloads our reverse shell and then executes it, granting us access!

Now it times to explore and find interesting files. Heading into the zico directory there is a to_do.txt file which looks promising.

This immediately sets off the alarm that we should check out the wordpress folder, and more specificaly the config file.


Nice, we have a username and a password. Perhaps this will work with SSH?

And yep! We are in on the zico user. Taking a look at what can be executed as superuser/root there are two things, but I couldn't find an interesting way to use them. After researching this when I was done, it seems there is a neat trick to use zip, which I will tuck away in my bag of tricks for another day. Instead, I opted to do some more Exploitdb research and came across a good exploit that could be used with this version of Ubuntu.

Copying the source code, we can bring up vim and paste it in, and then compile and run according to the source notes.


Awesome--we are root now and we got the flag! GG!
0 comments:
Post a Comment
Note: Only a member of this blog may post a comment.